Linux Basic Directory structure :
- bin – This directory is used to store the system’s executable files. Most users are able to access this directory as it does not usually contain system critical files.
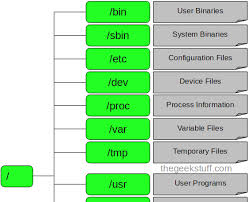
- etc – This folder stores the configuration files for the majority of services and programs run on the machine. These configuration files are all plain text files that you can open and edit the configuration of a program instantly. Network services such as samba (Windows networking), dhcp, http (apache web server) and many more, rely on this directory! You should be careful with any changes you make here.
- home – This is the directory in which every user on the system has his own personal folder for his own personal files. Think of it as similar to the ‘My Documents’ folder in Windows. We’ve created one user on our test system by the name of ‘sahir’ – When Sahir logs into the system, he’ll have full access to his home directory.
- var – This directory is for any file whose contents change regularly, such as system log files – these are stored in /var/log. Temporary files that are created are stored in the directory /var/tmp.
- usr – This is used to store any files that are common to all users on the system. For example, if you have a collection of programs you want all users to access, you can put them in the directory /usr/bin. If you have a lot of wallpapers you want to share, they can go in /usr/wallpaper. You can create directories as you like.
- root – This can be confusing as we have a top level directory ‘/’ which is also called ‘the root folder’.
The ‘root’ (/root) directory is like the ‘My Documents’ folder for a very special user on the system – the system’s Administrator, equivalent to Windows ‘Administrator’ user account.
This account has access to any file on the system and can change any setting freely. Thus it is a very powerful account and should be used carefully. As a good practice, even if you are the system Administrator, you should not log in using the root account unless you have to make some configuration changes.
It is a better idea to create a ‘normal’ user account for your day-to-day tasks since the ‘root’ account is the account for which hackers always try to get the password on Linux systems because it gives them unlimited powers on the system. You can tell if you are logged in as the root account because your command prompt will have a hash ‘#’ symbol in front, while other users normally have a dollar ‘$’ symbol.
- mnt – We already told you that there are no concepts of ‘drives’ in Linux. So where do your other hard-disks (if you have any) as well as floppy and cdrom drives show up?
Well, they have to be ‘mounted’ or loaded for the system to see them. This directory is a good place to store all the ‘mounted’ devices. Taking a quick look at our diagram above, you can see we have mounted a cdrom device so it is showing in the /mnt directory. You can access the files on the cdrom by just going to this directory!
- dev – Every system has its devices, and the Linux O/S is no exception to this! All your systems devices such as com ports, parallel ports and other devices all exist in /dev directory as files and directories! You’ll hardly be required to deal with this directory, however you should be aware of what it contains.
- proc – Think of the /proc directory as a deluxe version of the Windows Task Manager. The /proc directoy holds all the information about your system’s processes and resources. Here again, everything exists as a file and directory, something that should’t surprise you by now!
By examining the appropriate files, you can see how much memory is being used, how many tcp/ip sessions are active on your system, get information about your CPU usage and much more. All programs displaying information about your system use this directory as their source of information!
- sbin – The /sbin directory’s role is that similar to the /bin directory we covered earlier, but with the difference its only accessible by the ‘root’ user. Reason for this restriction as you might have already guessed are the sensitive applications it holds, which generally are used for the system’s configuration and various other important services. Consider it an equivelant to the Windows Administration tools folder and you’ll get the idea.
